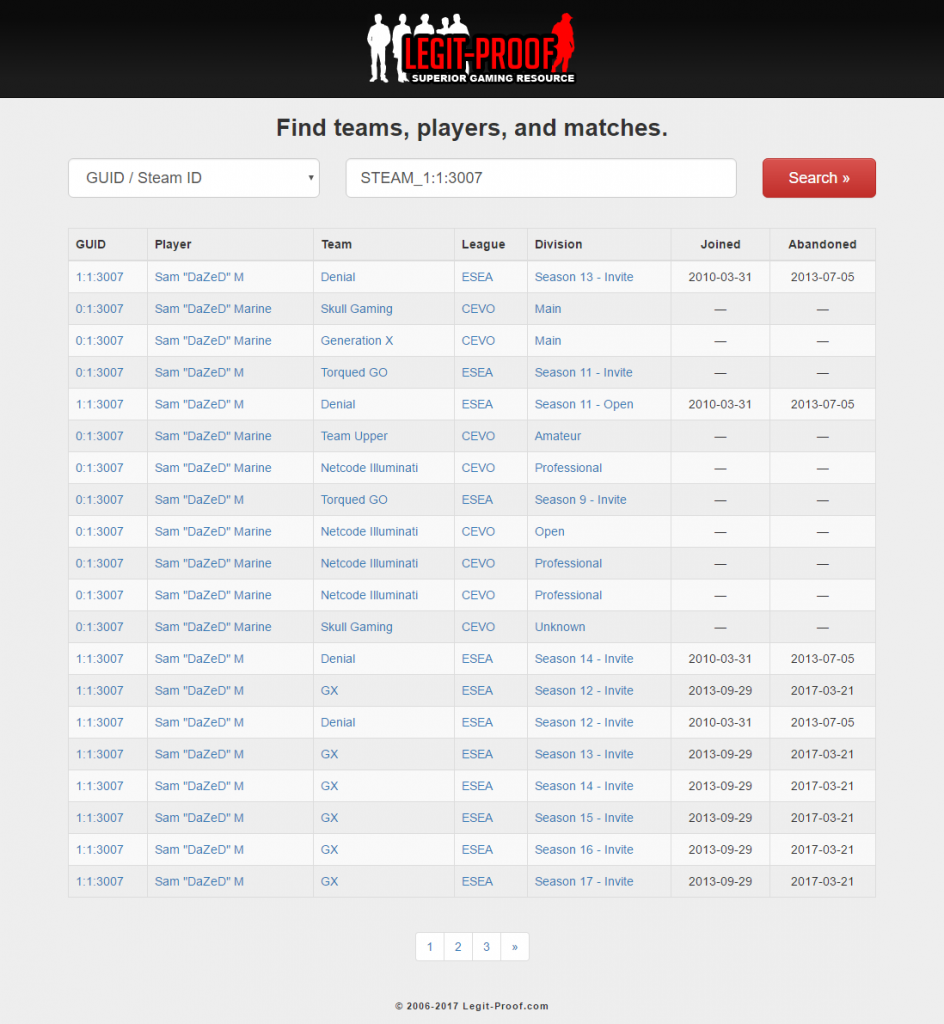
Companies exchange data between their internal departments, third-party vendors, web services, customers, and even robots! Data Integration is the name of the game. The key objective in successful data integration is securely transmitting information between systems, transforming incompatible data formats, and efficiently processing the data.
Secure Data Transmission
A savvy internet user is mindful of the websites they visit and pay attention to the green SSL security icon in their browser especially when visiting pages where they may enter sensitive personal information. Websites secured by the SSL protocol are usually distinguished by a URL that starts with “https://” in the browser window. For example, all Facebook pages sit behind SSL encryption.
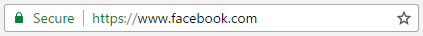
The SSL encryption protocol ensures that communication between a visitors web browser and the web server serving the web pages is encrypted and secure.
With that said, almost everyone surfing the internet today is aware of the need for security, but when it comes to data integration for companies, one protocol and method of protection may not cut it.
The amount of digital information increases tenfold every five years. Moore’s law, which the computer industry now takes for granted, says that the processing power and storage capacity of computer chips double or their prices halve roughly every 18 months.
Source: The Economist
Companies deal with extremely large data sets. Transferring vast amounts of information over the SSL secured HTTPS protocol is usually not the most efficient way of doing things, so different solutions are needed.
For example, SSH (SFTP) technology can be used to leverage the SSL protocol (already trusted for web browsing and online payments) for large data transfers. Sometimes companies need to integrate with third-parties that do not have automated software systems that deliver or consume data, which is why SFTP technology is wonderful in that a human can send data to an automated software system and vice versa.
Moving around large data sets is one problem, the subsequent challenge is validating that data is authentic and who sent it. This is where things get quite a bit more technical because the solutions entail encryption and decryption algorithms, certificates, tokens, and shared secrets. Contact Strategy Star to discuss solutions applicable to your business needs.
Data Format Transformation
It is established that companies must integrate with partners, vendors, and internal departments. Each party has their own systems and data formats that they are able to support. It is not unusual for two or more parties to find themselves in a situation where none of them are able to inherently support the data formats that their counter parts require. This is where data transformation comes in.
Some organizations deal exclusively in data formats produced by humans such as CSV, DOC, PDF, and XLS. Most software driven systems produce outputs and consume inputs exclusively in JSON or XML. Data transformation technology can be applied to convert these data formats in both inbound and outbound systems.
Strategy Star is experienced in developing data transformation solutions that enable integration between otherwise incompatible systems. Contact us to discuss data transformation solutions applicable to your systems and requirements.
Efficient Data Processing
Doing a lot of business means generating, consuming, and processing a lot of data. Data needs to flow in to your business, out of it, and within it. A single batch of data moving between organizations can easily exceed the Gigabyte (GB) threshold. When it comes to storing and archiving the data, things move in to the Terabyte (TB) range, and beyond! Processing data in these massive quantities can mean that manual workflows or poorly optimized software systems will become bottlenecks for your business and ultimately become a detriment to your bottom line.
Strategy Star can help your company redefine workflows and develop efficient software for processing the data that drives your business. You may already have existing software systems and if you are reading this, they are probably not good enough. We can review the systems you already have in place and design new, efficient software architecture that suits your business model and data needs.
“The rate at which we’re generating data is rapidly outpacing our ability to analyze it,” Professor Patrick Wolfe, Executive Director of the University College of London’s Big Data Institute, tells Business Insider. “The trick here is to turn these massive data streams from a liability into a strength.”
Source: Business Insider
Together we can get your data flowing again at top speed. Especially if you have been in business for a long time, you are probably running software that is old and was built for a world that does not exist anymore. Let’s turn your data from a liability into a strength. Contact us by email or phone.
You can read about our data triumphs with real-time network threat mitigation, e-sports data archiving, and competition data processing and analysis for tens of thousands of players and matches.